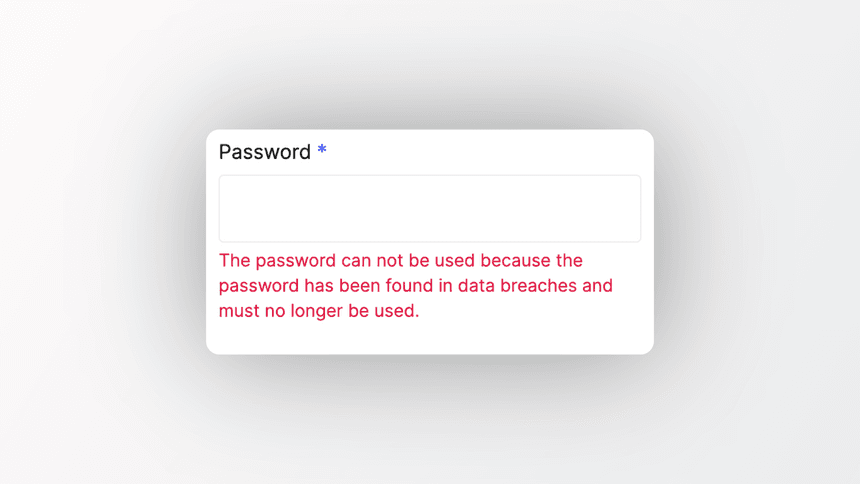
Why you need breached password detection
Criminals are always seeking opportunities to gain unauthorized access to organizational systems. As such, user accounts are a prime target in any organization.
Even though many companies have implemented passwordless authentication nowadays, passwords are still a common way to authenticate user accounts. While establishing a secure password etiquette would be a good solution, encouraging users to adopt best practices has proven to be unreliable.
Password breach detection is a clever and strategic solution to prevent leaked credentials from being used.
The risks of using leaked passwords
Leaked passwords are not an abstract or theoretical risk. Recent data breaches have affected major companies like T-Mobile, Optus, IKEA, Apple, Meta, TikTok, and Twitter, each compromising millions of user accounts.
info
The IBM Security Cost of a Data Breach Report reveals that the average total cost of a data breach globally in 2023 was $4.35 million. In the United States, the average total cost of a data breach in 2023 is significantly higher at $9.44M million. It takes an average of 9 months to identify and contain a data breach.
Compromised passwords from breaches can lead to fraudulent transactions and account takeovers, resulting in businesses facing substantial customer service and chargeback costs. A recent study predicts that fraudulent online transactions will cost merchants $206 billion between 2021 and 2025.
Additionally, breaches provide fertile ground for hackers, who trade passwords to take over a multitude of other accounts, for services such as email, banking, e-commerce, payments, and others.
How you can prevent poor password practices
Users often have poor password habits and previous attempts to solve this problem through increasingly complex password policies have not been successful. In fact they often led to users seeking to meet minimal requirements rather than creating secure passwords.
Due to the often confusing and contradictory password policies, remembering multiple passwords with different requirements is difficult for users, leading them to reuse passwords despite the risks.
info
Studies have shown 85% of users reuse the same passwords for multiple if not all personal and work accounts.
Modern password-breaking software makes use of a vast collection of leaked passwords to break into accounts. This is why it is important to check if a password has been leaked before allowing a user to use it.
NIST recommendations for breached password detection
The National Institute of Standards and Technology (NIST) recommends breached password detection systems that verify user-provided passwords against collections of previous breaches and dictionaries.
If a user's password is found to be compromised, NIST suggests forcing the user to select a different password while providing an explanation for the rejection.
It is important to let users know why their password was rejected, not only to inform users about compromised accounts. But also to not cause frustration and confusion as to why their favourite password is not accepted.
tip
Read about password policy best practices in the Ory documentation to get an overview of NIST recommendations on how to design a secure and usable password policy.
Effective solutions for tackling password breaches in a modern cloud environment
Traditional password hygiene practices place the full responsibility to take proactive measures on the user, whereas breached password detection provides an automated solution to prevent the use of compromised passwords.
Some organizations choose to create their own data ingestion system and breached password detection API, allowing for custom dictionaries and greater control over the system's design. However, this approach requires significant resources and expertise to develop and maintain.Unless your use case requires it, Ory recommends to make use of third-party APIs that provide reliable and easy-to-use solutions to implement breached password detection.
Breached password detection ♡ multifactor authentication
By employing breached password detection at the signup stage, organizations can proactively prevent compromised credentials from entering the system.
However, doing periodic checks for breached passwords holds little security advantage. The instant criminal actors gain access to a leaked password, they exploit it and look to escalate their access. They will not wait around for the periodic check to catch the leak. A periodic check for leaked passwords will help only in the rare edge case that the check is done in the small time frame between the password getting leaked and the bad actor getting access to the leaked password.
How do we stop bad actors when passwords for existing accounts are leaked?
The answer is multi-factor authentication. If the account's password is compromised the attacker will not be able to access it if a second factor has been added. This powerful combination effectively safeguards against the exploitation of leaked or breached passwords and holds a good balance between usability and security.
Protect your users and business from password threats
Humans are messy and unpredictable, and they often make mistakes.
This is why organizations require automated threat detection and incident
response management for effective security. Breached password protection
automates the identification of breached password risks to ensure application
security and protect customers.
All passwords entering Ory Network are checked by default against a vast collection of almost 1 billion leaked passwords by the industry leading haveibeenpwned.
As always with Ory this feature is open source, as are all other security relevant features.
Breached password detection for enhanced security today
In summary:
- Adopting a breached password detection solution is an effective approach to address the issue of breached passwords without relying on changes in user behavior.
- Implementing breached password detection reduces the risk of unauthorized account access by preventing the use of compromised passwords.
- Breached password detection protects applications and systems by preventing any leaked password from entering the system.
- Ory provides protection against common threats, offers comprehensive documentation, support, and 24/7 assistance.
tip
Sign up for a free developer account today, give Ory a star on GitHub, or reach out to the team to learn how you can adopt breached password detection.